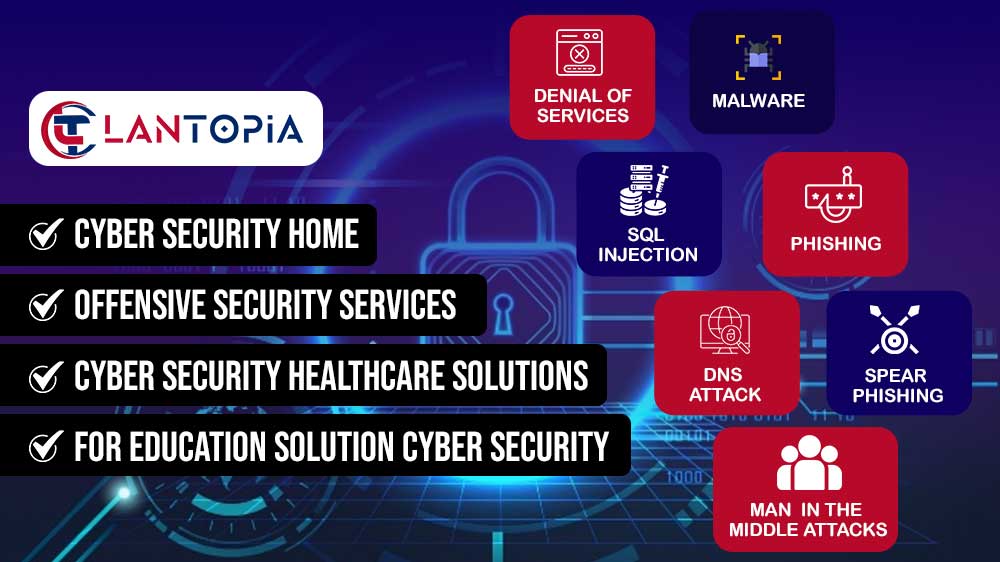
- Risk Assessment and Management
- Access Control and Authentication
- Network and Endpoint Security
- Regular Software Updates and Patch Management
Lantopia.com is a cybersecurity provider that specializes in providing cybersecurity solutions to small and large businesses.
cybersecurity solutions include a range of cybersecurity where we will support, improve your cybersecurity environment. A list of our fee structures is provided below. You can hire us on hourly or retainer basis to complete the work/task. The most cost-effective would be a monthly retainer that takes into account your needs. It also allows LANtopia to secure personnel to take care of your needs.
What can you expect to pay? We believe in staying ahead of the curve with our pricing because we respect our customers.
- Remote services are billed at $50/hr
- On-site services are $100/hr with a travel fee of $100 per visit
- A monthly retainer starts from $500 which accounts for 15 remote hours of support. This adds 50% bonus support hours for free and is the most economical and preferred by our customers.
What can you expect to get?
Dedicated cybersecurity professional with deep knowledge of the technologies needed to help your business. Recommendations on best practices. Fast turnaround and highest quality work with a proven track record.
We guarantee satisfaction or your money back.
- Risk Assessment and Management
- Assessments Conduct regular cybersecurity risk
- Vulnerabilities and Identify and prioritize potential threats
- Implement risk management strategies and Develop
- Employee Training and Awareness
- Provide training for all employees on cybersecurity
- Social engineering and Raise awareness about phishing attacks
- Reporting suspicious activities for Establish protocols
- Access Control and Authentication
- Policies Implement strong passwords
- (MFA) multi-factor authentication Enforce for sensitive accounts
- Update user access permissions and Regularly review
- Network Security
- The internal network Uses firewalls to protect
- Prevention systems and Employ intrusion detection
- patch network devices and software Regularly update
- Endpoint Security
- Antivirus and Anti-malware software Install and update
- Response (EDR) solutions and Implement endpoint detection
- Manage security and Monitor settings on all devices
- Data Encryption
- Encrypt sensitive data in transit and at rest
- Use secure protocols (SSL/TLS) for communication
- Implement encryption for removable storage devices
- Incident Response and Planning
- incident response plan Develop
- Conduct regular drills to test incident response procedures
- Establish a clear chain of communication during incidents
- Regular Software Updates and Patch Management
- Keep operating systems, software, and applications up-to-date
- Establish a patch management process to address vulnerabilities
- Regularly test patches in a controlled environment before deployment
- Backup and Recovery
- Implement regular data backups with offsite storage
- Test backup restoration processes to ensure data recoverability
- Develop a comprehensive disaster recovery plan
- Secure Configuration and Vendor Management
- Follow secure configuration guidelines for hardware and software
- Regularly audit and review system configurations
- Vet and monitor the security practices of third-party vendors
- Phishing Protection
- Implement email filtering to detect and block phishing attempts
- Train employees to recognize and report phishing emails
- Conduct simulated phishing exercises to assess awareness
- Mobile Device Security
- Enforce security policies for mobile devices
- Use mobile device management (MDM) solutions
- Enable remote wipe capabilities for lost or stolen devices
- Web Security
- Use secure browsing protocols (HTTPS)
- Employ web filtering tools to block malicious websites
- Regularly update and patch web servers and applications
- Security Audits and Compliance
- Conduct regular internal and external security audits
- Ensure compliance with industry-specific regulations
- Address any non-compliance issues promptly
- Physical Security
- Restrict physical access to servers and network equipment
- Implement security measures for data centers and server rooms
- Monitor and log physical access to sensitive areas
- (SIEM) Security Information and Event Management
- Implement SIEM solutions for centralized log monitoring
- Analyze and respond to security events in real time
- Generate reports on security incidents and trends
- Collaboration and Communication Security
- Secure communication channels, including email and messaging
- Implement encryption for communication tools
- Train employees on secure collaboration practices
- Insurance and Legal Considerations
- Consider cybersecurity insurance to mitigate financial risks
- Stay informed about legal and regulatory requirements
- Engage legal counsel for cybersecurity compliance
- Improvement and Continuous Monitoring
- For cybersecurity Establish a continuous monitoring system
- update cybersecurity policies and Regularly review them
- Learn from incidents to improve cybersecurity practices