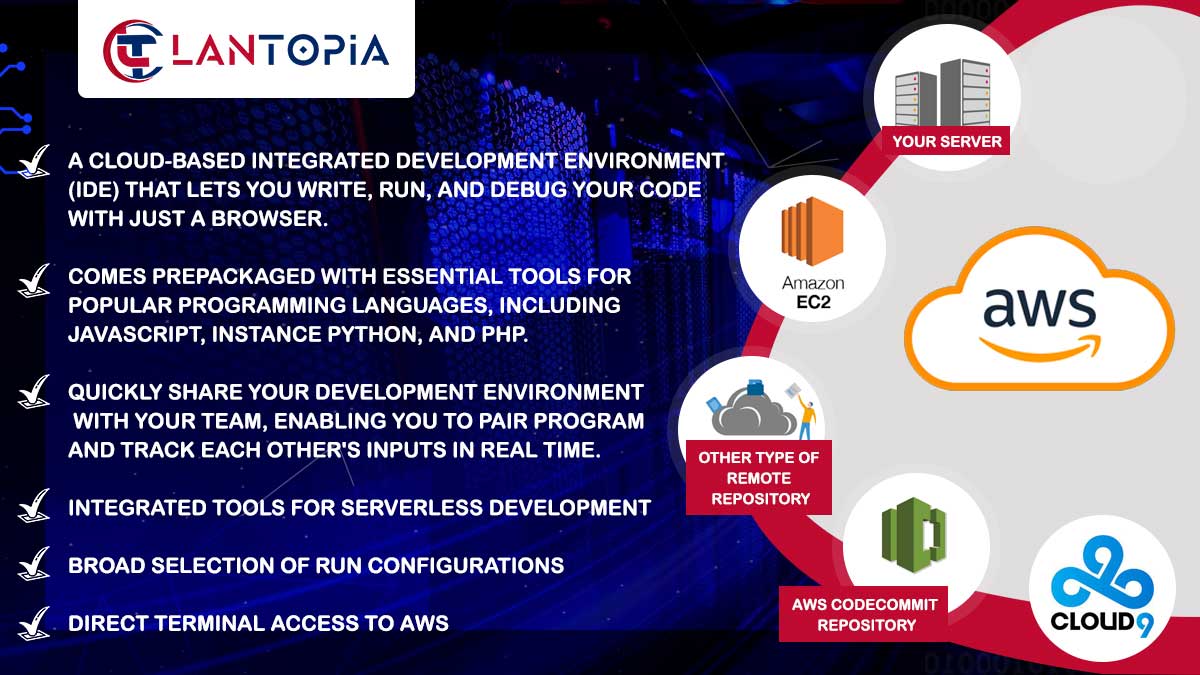
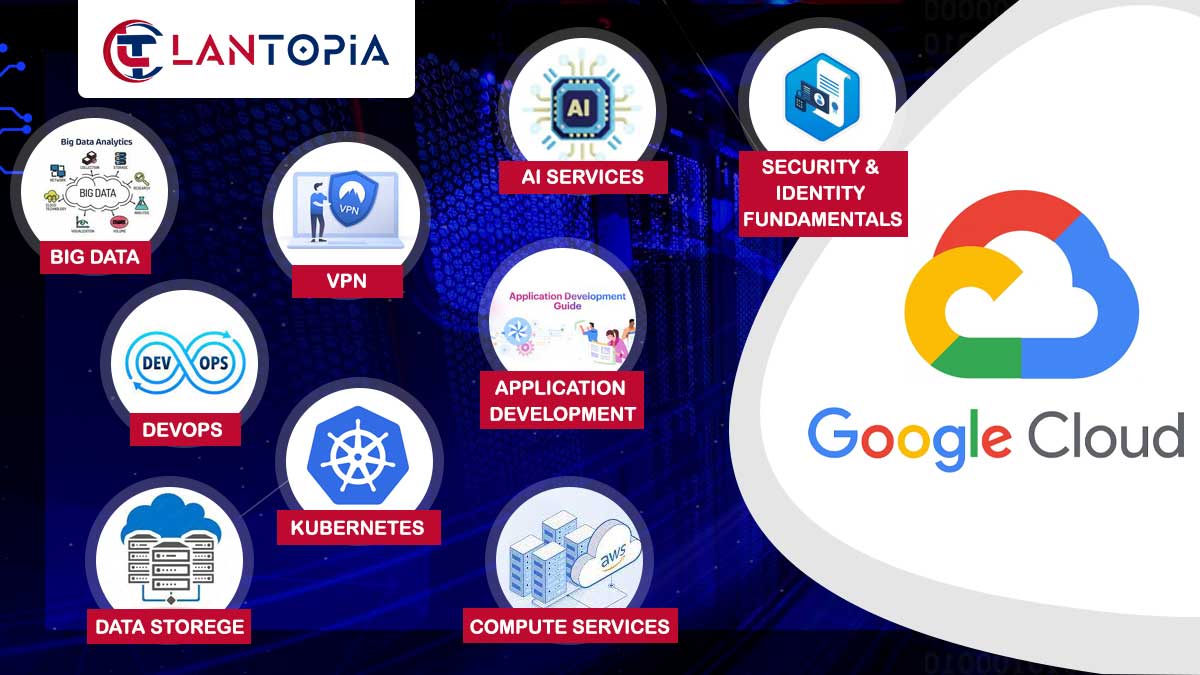
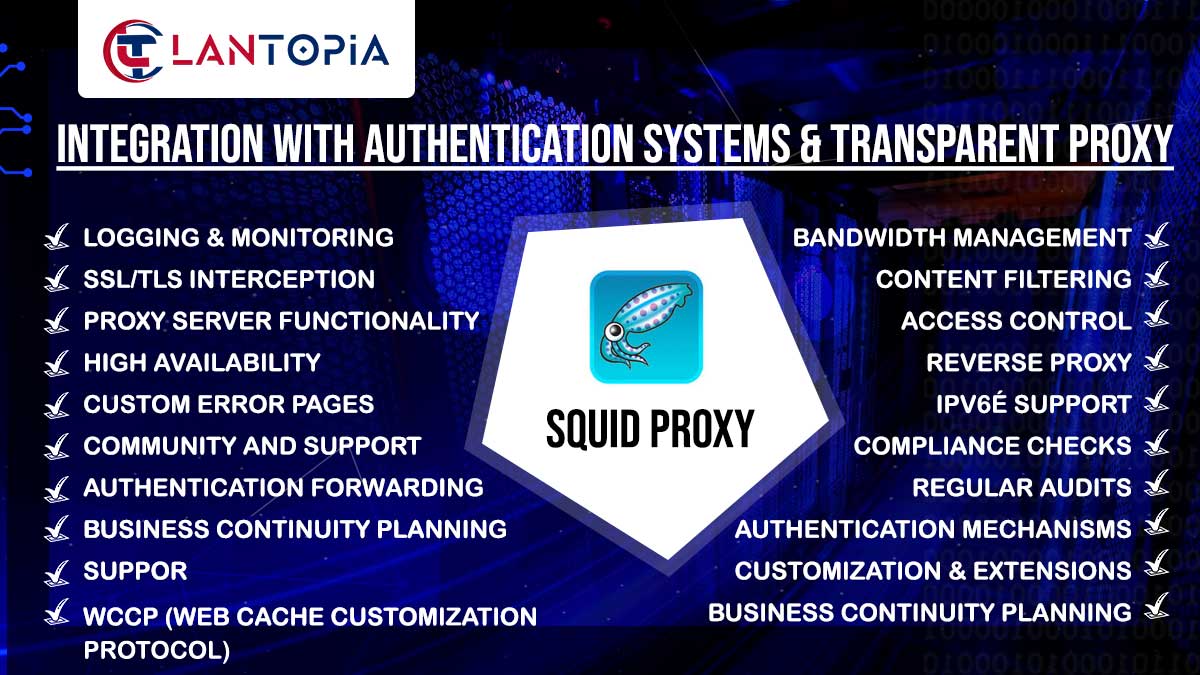
- Integration with Identity Management and Multi-Environment Support
- Device Enrollment, Platform Compatibility and Security Policies
- Mobile Threat Defense (MTD) and Remote Wipe and Lock
- Application Management and Compliance Monitoring
What can you expect to pay? We believe in being up-front with our prices as we respect our customers.
- Remote services are billed at $50/hr
- On-site services are $100/hr with a travel fee of $100 per visit
- A monthly retainer starts from $500 which accounts for 15 remote hours of support. This adds 50% bonus support hours for free and is the most economical and preferred by our customers.
What can you expect to get?
Dedicated IT professional with deep knowledge of the technologies needed to help your business. Recommendations on best practices. Fast turnaround and highest quality work with a proven track record.
We guarantee satisfaction or your money back.
Device Enrollment
- Streamline and automate the enrollment of mobile devices into the MDM system
- Support various enrollment methods, including manual, automated, and bulk enrollment
Platform Compatibility
- Ensure compatibility with a variety of mobile platforms (iOS, Android, Windows)
- Choose an MDM solution that supports the specific devices used in the organization
Security Policies
- Define and enforce security policies for mobile devices
- Implement password requirements, encryption, and device lock settings
Application Management
- Manage the deployment and updating of mobile applications
- Support both in-house and third-party applications
Remote Wipe and Lock
- Implement remote wipe and lock capabilities for lost or stolen devices
- Ensure the secure removal of corporate data from compromised devices
Compliance Monitoring
- Continuously monitor devices for compliance with security policies
- Automatically remediate non-compliant devices or restrict access
Device Inventory
- Maintain an up-to-date inventory of all managed mobile devices
- Track hardware and software details for each device
Containerization and Dual Persona
- Implement containerization to separate corporate and personal data
- Enable dual persona solutions for managing work and personal profiles
Geolocation Tracking
- Enable geolocation tracking for locating lost or stolen devices
- Use geofencing to enforce security policies based on device location
Mobile Content Management (MCM): Implement Mobile Content Management to secure corporate data on devices. Control access to sensitive documents and data.
Over-the-Air (OTA) Updates: Facilitate over-the-air updates for operating systems and security patches. Schedule updates during non-disruptive times to minimize user impact.
App Whitelisting and Blacklisting: Define policies to whitelist approved applications. Blacklist unauthorized or potentially harmful applications.
Device Decommissioning: Establish processes for decommissioning devices when they are no longer in use. Ensure secure removal of corporate data during decommissioning.
User Authentication: Implement strong user authentication methods for device access. Utilize biometric authentication, PINs, or tokens for added security.
Mobile Threat Defense (MTD): Integrate Mobile Threat Defense solutions to detect and mitigate mobile threats. Monitor for malware, phishing, and other security risks.